BazarLoader Targets “Slack” and “BaseCamp” Collaboration Tools To Hook Enterprise Employees, Sophos Reports
Series of Malicious Spam Campaigns Includes One Delivering Malware Via Phone Operators
A spam message sent to a target on BaseCamp
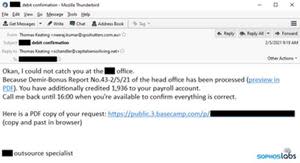
SophosLabs research shows how a BazarLoader attack targeting a BaseCamp user was personalized with the recipient’s name and company name embedded in the message
A “BazarCall” spam message

SophosLabs research shows how spam emails threaten targets with fake online service renewal fees to lure them into calling a phone number where a human operator will try to guide them towards installing BazarLoader malware
OXFORD, United Kingdom, April 15, 2021 (GLOBE NEWSWIRE) -- Sophos, a global leader in next-generation cybersecurity, has published new research, “BazarLoader Deploys A Pair of Novel Spam Vectors,” detailing two malicious spam campaigns that began in January, 2021. The first targeted remote working employees at larger businesses, using accounts on the Slack and BaseCamp websites to temporarily host the malware and deliver it directly to targets. A second campaign warns recipients they are about to be charged for an online service and asks them to call a number where a human phone operator shares a weblink that will lead them to the malware.
The Sophos research shows how the attacks targeting Slack and BaseCamp users were personalized with the recipient’s name and company name embedded in the message. The messages claimed to contain important information relating to payroll, contracts, invoices or customer service inquiries, and even, in one case, a layoff notification. The BazarLoader infection was triggered as soon as a recipient opened the document tied to the message, or clicked on the link. There were two versions of the BazarLoader malware used in the campaign. One was a loader for other malicious payloads, while the other was BazarLoader’s own backdoor.
A spam message sent to a target on BaseCamp:
A photo accompanying this announcement is available at https://www.globenewswire.com/NewsRoom/AttachmentNg/417c437b-4769-4ebb-b6dc-bcf901f8fb79
The second spam campaign has been named “BazarCall.” The spam messages claim the recipient’s free trial for an online service is about to expire and they urgently need to call a telephone number embedded in the message in order to opt-out of an expensive, paid renewal. People who call the number are given a web address they need to visit to unsubscribe from the service. If they click the “unsubscribe” button on that web page, the page delivers a malicious Office document that, when opened, infects the computer with BazarLoader malware.
A “BazarCall” spam message:
A photo accompanying this announcement is available at https://www.globenewswire.com/NewsRoom/AttachmentNg/f9baa779-5e12-4eff-b083-ddc1ec3a99c3
After the attackers breach a target, they inject BazarLoader malware into the memory of legitimate system processes, where it can hide undetected by security tools. As a loader, it is capable of delivering a wide range of potentially devastating attacks against the enterprise, including ransomware.
“BazarLoader first appeared about a year ago, delivering ransomware such as Ryuk and other malware, sometimes alongside Trickbot,” said Andrew Brandt, principal threat researcher at Sophos. “Our analysis of BazarLoader’s behavior and characteristics suggests the attackers may be experimenting with new approaches to target high-value businesses.
“The attacks on enterprise employees through the Slack and BaseCamp platforms lasted just a few weeks. This could be because brazenly hosting malware in accounts on a trusted platform is a very short-lived opportunity – the accounts were taken offline within hours of us reporting them. The campaign that followed seems remarkably convoluted, requiring recipients to call a helpline and then take a series of actions: clicking on a link, hunting for an elusive ‘unsubscribe’ button that we eventually spotted buried deep in the FAQ section, downloading a document, and opening the document… before finally getting stung with the malware.”
From a technical perspective, Sophos researchers found signs that BazarLoader’s developers have been advancing the malware’s features and functionality. Some of these advancements, like obfuscation and encryption, strengthen the malware’s ability to evade detection. Further, the malware encrypts all traffic to its command-and-control servers.
Sophos researchers have been able to fully deconstruct communications between the BazarLoader malware and its command-and-control servers during these attacks. Among other things, they uncovered the use, possibly also experimental, of a blockchain DNS service. This type of DNS service may prevent authorities from seizing or shutting down the domains linking to the malicious infrastructure. Sophos researchers further observed a number of similarities and connections between BazarLoader and Trickbot, which add weight to the belief that BazarLoader has been created, and is operated by the same threat actors who built Trickbot.
Sophos endpoint protection products will block and report BazarLoader behaviors as Evade_18a or HPmal/Crushr-BJ.
Sophos has published indicators of compromise for BazarLoader to SophosLabs Github.
Sophos Intercept X protects users by detecting the actions and behaviors of malware like BazarLoader, including scanning for suspicious activity in memory and protecting against fileless malware.
Further information on BazarLoader and other cyberthreats is available at SophosLabs Uncut.
Additional resources
Sophos reports extensively on ransomware. Recent research includes a three-part analysis of Conti ransomware and a series of articles on the new threats DearCry and Black Kingdom taking advantage of the ProxyLogon Exchange vulnerabilities
Learn more about Sophos’ Rapid Response service that contains, neutralizes and investigates attacks 24/7
The four top tips for responding to a security incident from Sophos Rapid Response and the Managed Threat Response Team
CONTACT: Hanah Johnson sophos@marchcomms.com

 Yahoo Finance
Yahoo Finance 