A new flaw in a Bluetooth at-home COVID-19 test could produce false results
A security researcher has discovered a bug in Cue Health’s at-home COVID-19 testing kit that could allow users to falsify results.
Cue Health's COVID-19 testing kit is a Bluetooth-operated molecular test that can detect a positive specimen in 20 minutes. The system tests for coronavirus using a nasal swab that is inserted into a single-use cartridge and analyzed by the battery-powered Cue Reader, and this then transmits the result over Bluetooth to the Cue Health app on the test-taker's phone. In March 2021, Cue’s system became the first molecular COVID-19 testing kit to receive emergency authorization from the FDA for at-home and over-the-counter use.
While the FDA at the time applauded Cue Health's innovative approach to COVID-19 testing, Ken Gannon, a security consultant at WithSecure, F-Secure's corporate security business, found a flaw in the testing kit that could allow test results to be modified.
It's the second time a security vulnerability has been discovered in a connected COVID-19 test by the same researcher who recently exposed a similar flaw in Ellume’s COVID-19 Home Test, calling into question the integrity of testing kits rushed to market under the federal government's emergency approval powers.
The vulnerability — now fixed — was found in how the Cue Reader communicates with the Cue Health app over Bluetooth using the Protobuf protocol, which presents the test data in an easily readable block of data. The block of data generated by the Reader ends in “10 02” for a positive COVID-19 test result, or “10 03” for a negative result. Gannon developed a script that enabled him to intercept and modify the data by manipulating these digits. By changing a single digit in the result, or "bit-flipping," Gannon could change his negative result to a positive result, as well as to obtain a certificate verifying the results as valid.
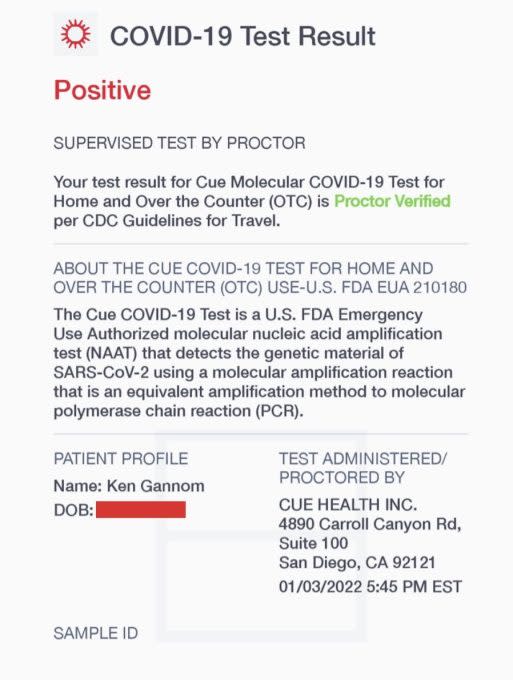
A manipulated COVID-19 test result. Image Credits: Ken Gannon / WithSecure
“The process is basically the same for changing a positive result to negative, which could cause problems if someone who knows how to do what I did decides to start falsifying results,” said Gannon. Negative COVID-19 tests have become requirements for many activities, including traveling into the United States.
“As of right now, the skill level required to flip those bits is somewhat high," Gannon said. "A person would need to have decent knowledge into hacking mobile applications and running custom code within Cue’s application. However, one thing I’m always worried about with Android application hacking is the ability to customize the hack so that the average consumer can do the same hack. Because of this, I’m purposely disclosing technical details and custom code that only reverse engineers could understand and use," he added.
Gannon shared his research with Cue Health, which said it is not aware of any falsified test results beyond those reported by WithSecure, but said it has added server-side checks aimed at detecting manipulated results. Cue Health did not respond to TechCrunch when asked if the company had the means to detect the manipulation of results prior to WithSecure's findings.
Users should also update to the latest version of the Cue Health app.

 Yahoo Finance
Yahoo Finance 